Protect Yourself from Email Spam
Everyone gets email spam, and while it can be a general annoyance, it can also be dangerous if you aren’t careful on how you manage it. In this blog post I wanted to share how I identify “dangerous” spam, and offer some of my own strategies to protect myself. The following email examples are from spam email I’ve received within the last 30 days.
Spam comes in three basic types
Solicitation spam – this type isn’t inherently dangerous since the purpose is simply to get you to visit a “legitimate” website or contact them by phone or email for the purpose of selling you a legitimate product or service.
Phishing spam – the purpose is nefarious, meaning the sender will misrepresent who they are in some way. Phishing will often include creating an email address (and fake website in some cases) to appear to be a legitimate business/organization. The goal is to get you to pay for some service, or to get personal information to steal your identity.
Hacker spam – this type of spam is related to phishing spam, and is the most dangerous since the email will contain a link or file that upon being clicked will install a trojan or virus of some type. The purpose is typically to infect your computer to retrieve personal information, or to provide them remote control of your email application and/or computer to send spam emails or to overwhelm a server.
Protection strategies
1. Use a reputable webmail server for email.
Webmail is always a better option than using one’s hosting server for email, or using Outlook since the emails are downloaded onto one’s personal computer. The best free webmail option is GMAIL since Google has very good spam and virus protection filters. If you need domain specific email for a business Google’s “Business Mail” or GoDaddy’s webmail are good options. Both of the later will cost approx. $5/mo per email address.
Note: We don’t recommend Hotmail, Yahoo mail, etc since these are often associated with spam accounts and will often be blocked by ISPs. And as noted above, don’t use your hosting account for webmail (either direct access or with Outlook) since hosting email servers are often exploited, and this can easily get one’s website server infected with a virus/trojan.
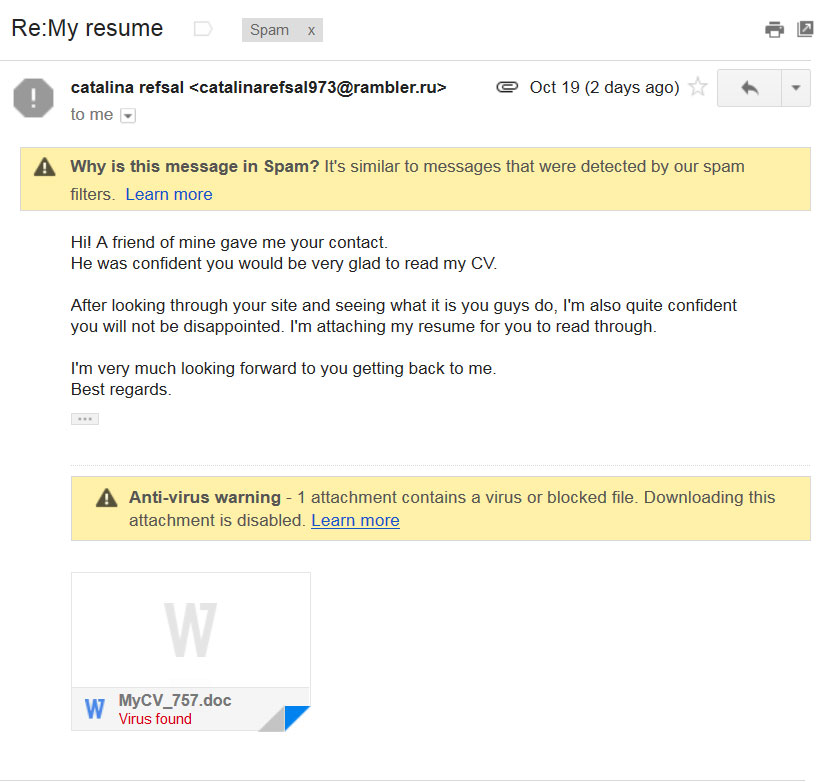
2. Never click on a link or graphic (which often are hyperlinked) unless you absolutely trust the email’s sender.
It is not dangerous to open an email, but once a link is clicked you have “executed” a scripting process, or action in some way. A good email server will catch “most” virus/trojans, but it is best to be overly cautious in this regard. Note that Word Docs are a common way to include malicious scripting, as are PDFs, Flash, and Java applications.
3. Evaluate the sender’s email address and content of email.
You can tell a lot about “who” the sender is by looking at the sender’s email address. In many cases the email will be slightly different from a legitimate “domain” address. Common options include the addition of a prefix or suffix and/or a different different domain extension than the one used by the business/organization.
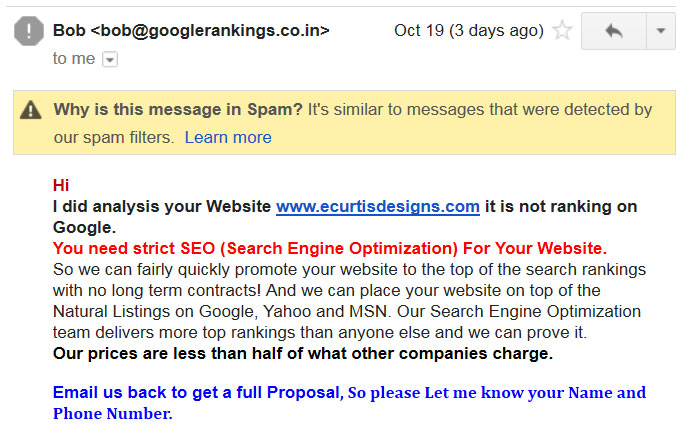
The following email shows that the sender attempted to appear legitimate by adding “googlerankings” to their email address. The addition of “.co.in” let’s me know that this business is from “India”.
In addition to the email address itself, one can tell a lot about the sender by how the email is formatted. In the example above there is no spacing between the first and second paragraph. In this case a “script” was used that automatically sends emails to web addresses harvested online with the recipient’s domain included to attempt to personalize the email. The sender also asks that you provide your name and phone number (which you should not provide). The important thing to recognize is that the majority of spam emails of all types will not include a web address, a contact phone number, or a business address as any “legitimate” business would provide.
Note: if you are unsure on whether a web address is legitimate just search the name of the business in Google. If the site comes up “without a warning of some type” and the address provided in the email matches the one online then the business is legitimate. This is the only sure way to authenticate a business.
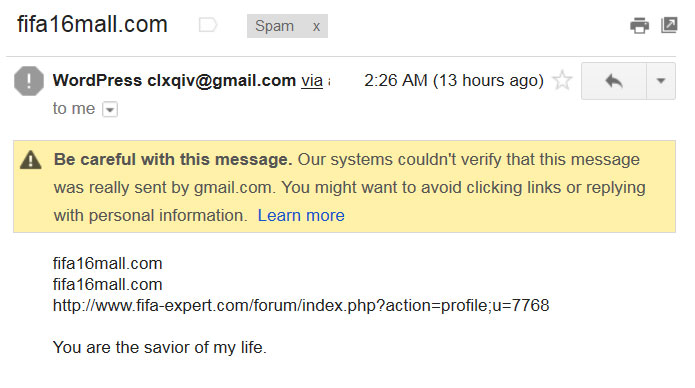
The next email sample is of a type commonly found in my spam box. As Gmail’s notice notes, “our system couldn’t verify that the message was really sent by Gmail”. Remember that any email address can be created that is “forwarded” to another, this is why forwards are often blocked or delegated to one’s spam box by ISPs. In this email example the message merely links to some nefarious website with the addition of text to pique one’s curiosity. The from address indicates that the email was sent from a WordPress website which may or may not be true.
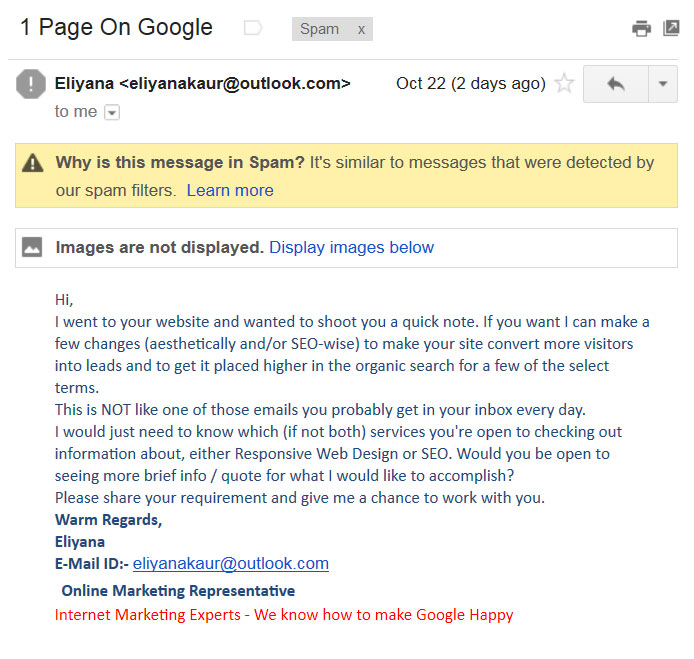
The next email sample has an “outlook” suffix for the email sender’s address. Not long back Hotmail re-branded itself as Outlook.com. As noted above “hotmail” is a common source of spam emails since the email server is not authenticated which allows for a variety of fraudulent activities. As a rule I am suspicious of any email that is sent from an email address that isn’t a verified Gmail address, or a domain specific address (domain specific requires authentication). When evaluating this email I see that there is no spacing between the content blocks (paragraphs), and no website. As noted above, any “legitimate” business that sends you email will include a web address and contact phone number, and most will take to locate your name, as well as visually format the email correctly.
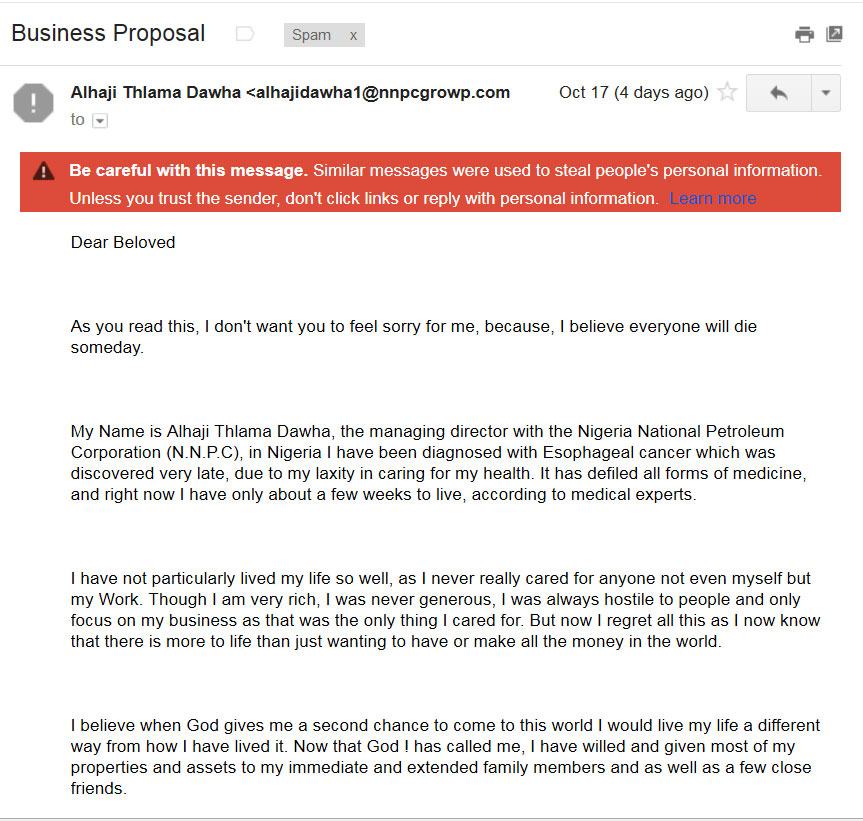
This last example is the most amusing type I get, and to my eye is the easiest to see as spam. In the case of this email Google has clearly noted that the intention is to “steal people’s personal information”. Okay, so the title of the email is “Business Proposal” and the email starts with “Dear Beloved”, and the body content has excessive spacing between paragraphs.
There are several varieties of this type of email. In most cases there is some sad story followed by a request to provide assistance in some way. In many cases there is a promise of financial compensation by helping them retrieve money in some way.
Note: the URL of the sender’s email address is nnpcgrowp.com This is an attempt to fool one in thinking that the email is from the nnpcgroup.com, which is the Nigerian National Petroleum Corporation. Clearly “group” is not spelled “growp”.
Please note that spam email can also come from people you know. I have received spam emails from clients, friends, and my sister. In each case their email server was taken over by a hacker/spammer. When you evaluate an email (from any source) there are tell-tale indicators that will let you know if the email is legitimate. If an email is taken over there will typically be several emails indicated in the “to” address field, or within the “CC” (in some cases the BCC will be used which is not visible to the recipient). In addition, the message will always seek to get you to “click a link” or perform some other such action. If you are unsure if the email is legitimate just contact them by phone and ask them if they did in fact send it?