Online security is important! I have been Online since the WEB was first available, and rarely a day goes by where someone hasn’t tried to compromise my business website, Spam my blog, or seek to acquire personal information from some form of social engineering attack. Many of my clients send me emails they receive and ask me if they are legitimate, and in most cases they are a scam of some type, and often an attempt at exploitation. As for myself, some years back I provided my AOL access per a fraudulent request and found out soon that my email had been used to send porn to hundreds of people (not good). Since then I have seen hundreds of attempts to get my private information … pretenses that they were from my bank, PayPal, my hosting company, hosting server, trying to give my inheritance money for a processing fee, and more. Since many people are unfamiliar with the techniques used to compromise security I have taken some time to share some information and strategies.
Accordingly to statistics from the National Cyber Security Alliance approximately one in five Americans have been victimized by a crime via the Internet. Such attacks include social media such as Facebook, CMS and e-Commerce websites, email phishing, and phone and direct mail phishing. You can more about Online security at: https://www.us-cert.gov/cas/tips/ST04-014.html
Firstly, if you have an established CMS or e-Commerce website, or your website is using a database for a blog or other application, there is a good possibility that your website will be attacked. Higher profile websites get the most attacks which typically occur from SQL Injections and Cross-site scripting. The goal of the hacker is to acquire sensitive information such as credit card data, post malware, or too disrupt a site so as to take it off-line. SQL Injections allow the hacker to access the database and import their own data. This is often used to place Ads, links to malicious landing pages, etc into your pages. Malware is a script that is installed on your computer that is used to disrupt computer operation, gather sensitive information, or gain access to private computer systems. I personally track attacks on my website by logging the IP address, but other suggestions is to use encrypted FTP for uploading/downloading, and for the large business a WAF (Web Application Firewall) which filters all requests, blocking requests that match the pattern of common attacks such as SQL Injection and Cross-site Scripting. Imperva’s Cloud WAF is an affordable product for small to mid-enterprise businesses that offers the highest levels of website security without requiring a large equipment investment.
With the better CMS applications such as the new versions of WordPress and Joomla the chance of a SQL Injection is less common, yet many less popular applications and scripts have exploits. My suggestion is to do an Online search for exploits on any CMS system, e-Commerce, database driven application or script you plan to install, or less known free or commercial software purchased Online to see if there is any news about security vulnerabilities and exploits. I have found problems with scripts of all types, which include Forums, Calendars, Guest Books, etc. Not long back I had a client come to me with an existing site that had hundreds of Trojans which accessed their site via their mail server. It took me over a day to remove all the Trojans.
The other common attack method is commonly referred to as social engineering attacks. This is where hackers attempt to trick you into giving them privileged information over the phone or by email so they can gain access to your accounts or website. If you are thinking that you are too smart for something like this to happen, well, the list of institutions and companies that have been exploited in this way is very long, and includes Nato, Sony, Yahoo, LinkedIn, Walmart, etc. The primary strategy to avoid such attacks is to never give out your username and password (or other personal information) unless you are absolutely sure that the source is legitimate.
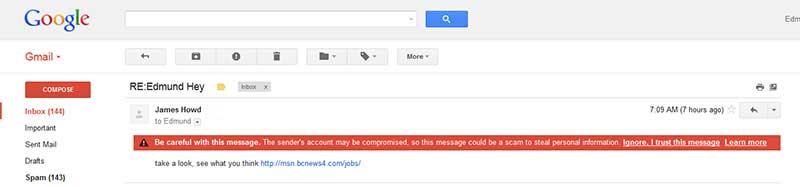
An email scam where a contact’s email was compromised to send a dangerous link
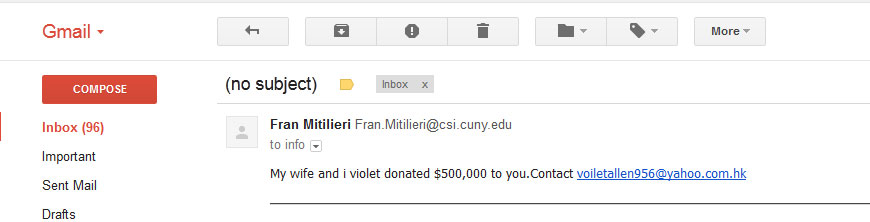
An email where a promise of money is noted.
Remember that is easy for a website designer to duplicate a website page, or an email with all associated images and branding, etc., and then mask the reply email address. If you use a good Web mail option such as GMAIL their Spam catcher will typically catch fraudulent emails since it checks the referring address, yet it won’t when they are sent through a contact’s email address as a result of a Trojan or other malware script. With the latter, typically there will be a line or two of text suggesting you click a link which would not be typical of most emails from a friend or regular contact.
This brings me to the other important consideration – never click a link in an email unless you are sure of its source. In many cases the email won’t have any text, just an image with which links, so same goes, don’t click it. For myself, if I receive an email from my bank, or other business/agency requesting personal information I will often contact them by phone (note that I call them directly) to ensure that the email is legitimate. If someone calls me requesting private access info I don’t provide my personal details; instead I ask them for a number to call them back, yet before I call them I check the validity of that phone number to ensure that it is associated with the specific institution. You can learn more about email phishing scams at: https://www.microsoft.com/security/online-privacy/phishing-symptoms.aspx
As for phishing attempts, here are some that I’ve encountered that you should look out for.
- Pretense that they are conducting a survey to justify the types of questions they are asking.
- Request that you help them collect money that is owed them wherein you will be compensated.
- Pretense that tells you that you have money owed you.
- Pretense that your account details need to be updated due to a software or security upgrade.
- Pretense that your account may be terminated if account details are not provided within a specified time frame.
- Pretense notice that suspect or fraudulent activity involving the user’s account has been detected and the user must therefore provide information urgently.
- Pretense that routine or random security procedures require that the user verify his or her account by providing the requested information.
In some cases the ruse is an attempt to get your username and password associated with a specific account. This could be your email, financial institution, etc. In other cases they seek to get you to provide your mother’s maiden name, social security number, driver’s license number, or call a phone number that is not toll-free, and instead costs you dearly. About.com lists the top 10 scams here: https://antivirus.about.com/od/emailscams/tp/onlinescams.htm
As final notes, if you think your computer has malware, be sure to use a good virus scan software (not an Online options since these are often fraudulent). McAfee, Norton, or Kaspersky are recommended. Whichever software you use be sure that it checks and has removal tools for both virus and Trojans. This is especially important if you use Outlook as your mail server since the mail is stored locally not on a Internet web server which will at least have some security protocols. In Facebook be careful not to install an APP unless you trust its source. And as noted above don’t install a software or script unless you can verify that it is safe. Many softwares, even common ones, will attempt to install unwanted aspects … such Adobe Flash updates trying to install McAfee, Quicktime installing the BING tool-bar, etc.
If you do get your information compromised then be sure to report it. You can do so at: https://www.us-cert.gov/nav/report_phishing.html